Services
- Home
- Services
Our Service Methodology
Success begins with building a team of experts who understand your project vision. You need to know there are clear, mutually understood project standards, as well as measurable information to demonstrate progress. You also need the flexibility to evolve requirements as they’re better understood — and a team with the flexibility to adjust course.
Our delivery methodology is comprised of Four phases – Planning, Design, Deploy, Validate and Launch. Throughout all phases of the project, we will deliver weekly status reports and have weekly status reviews that evaluate progress, as well as identify risks and issues.
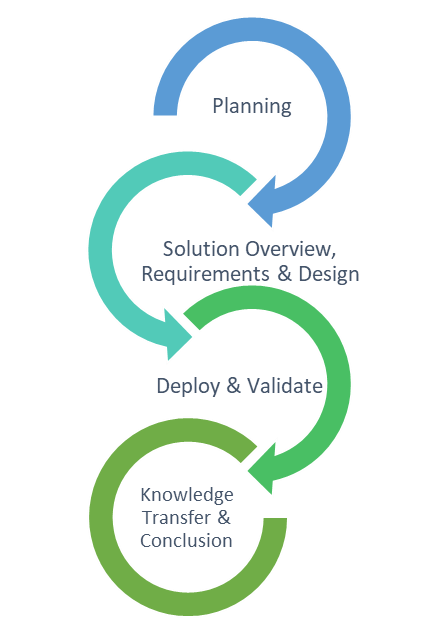
- Provide an overview of the proposed solution
- Understand and capture the business requirements and constraints
- Create an Architecture Design for the solution that can be reviewed by the customer stakeholders prior
- Deploy the designed solution into a production environment
- Conduct User Acceptance Testing to validate it meets the user’s needs
- Conduct Knowledge transfer sessions to enable the customer’s teams to properly manage the solution
Our services include
- Advanced Threat Protection
Utilizing state-of-the-art technologies to detect and neutralize threats before they can impact your business operations.
- Network Security
Ensuring your network infrastructure is fortified against intrusions and vulnerabilities through robust firewalls and intrusion detection systems.
- Endpoint Security
Providing advanced protection for all endpoints, from desktops to mobile devices, ensuring that every access point is secure.
- Data Encryption
Safeguarding sensitive information with strong encryption methods to prevent unauthorized access and data breaches.
- Incident Response
Offering a rapid response team ready to address and mitigate any security incidents, minimizing downtime and damage.
- Compliance and Risk Management
Assisting your organization in meeting regulatory requirements and managing risks effectively with tailored solutions.

